



Recently, we’ve implemented PPPoE Radius authentication on Cisco one of the most powerful BRASes ASR 9000, that runs the IOS XR operation system. There are two steps of the configuration – the first one is to make the PPPoE server work and request a Radius server and the second part is an advanced configuration with speed limitation definitions and COA configuration.
The first part is the basic configuration of IOS XR PPPoE Radius:
Radius server is reachable in VRF called DMZ :
aaa group server radius SPLYNX
vrf DMZ
server 172.16.0.20 auth-port 1812 acct-port 1813
key 7 014156547F5A070D321D1C5A395546
timeout 10
retransmit 5
source-interface XXXX (please define to be sure what IP will be used as NAS IP)!
aaa authorization network default group SPLYNX
aaa accounting network default start-stop group SPLYNX
aaa accounting service default group SPLYNX
aaa accounting subscriber default group SPLYNX
aaa authorization subscriber default group SPLYNX
aaa authentication subscriber default group SPLYNX
dynamic-template
type ppp SPLYNX_PPP_Chap
ppp authentication chap
keepalive 60 3
ppp ipcp dns 1.1.1.1 8.8.8.8
accounting aaa list default type session periodic-interval 5
ipv4 unnumbered Loopback10
!
type ppp dynamic-template
!
type service s1
ipv4 unnumbered Loopback10
!
!
interface Loopback 10
ipv4 address 192.168.50.1 255.255.255.0
subscriber
pta tcp mss-adjust 1430
!
pppoe bba-group SPLYNX_PPPOE
service selection disable
!
class-map type control subscriber match-any PPP
match protocol ppp
end-class-map
!
!
policy-map type control subscriber PPP_PM
event session-start match-first
class type control subscriber PPP do-until-failure
10 activate dynamic-template SPLYNX_PPP_Chap
!
!
event session-activate match-first
class type control subscriber PPP do-until-failure
10 authenticate aaa list default
!
!
end-policy-map
APPLYING ALL ON INTERFACE VLAN 200 under LCAP bundle :
interface Bundle-Ether1.200
ipv4 point-to-point
ipv4 unnumbered Loopback10
service-policy type control subscriber PPP_PM
pppoe enable bba-group SPLYNX_PPPOE
encapsulation dot1q 200
!
The second part of the configuration is related to COA/COD disconnection of the session when it’s initiated on Splynx and also to setting speed limits.
To achieve the PPPoE session disconnection from Splynx we should allow connection from Radius server to Cisco IOS XR device. The configuration for allowing incoming requests from the Radius server is following:
aaa server radius dynamic-author
port 3799
client 172.16.0.20 vrf DMZ
server-key 7 1446405858517C
We usually use port 3799 for it and it also should be defined inside Splynx Config → Radius → NAS settings:
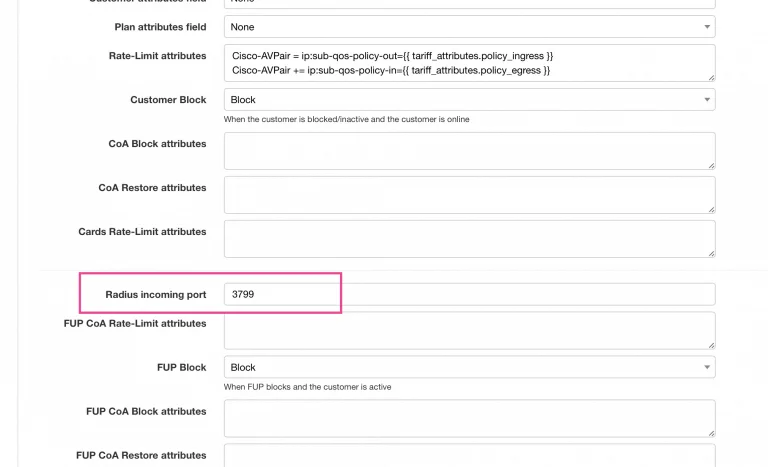
As you can see in the screenshot, there are also two rate limit attributes defined:
Cisco-AVPair = ip:sub-qos-policy-out={{ tariff_attributes.policy_ingress }}
Cisco-AVPair += ip:sub-qos-policy-in={{ tariff_attributes.policy_egress }}
These are the policy names that are setting the speed limitation for end-user. To set up the speed limits we added additional fields to Splynx Internet plans and then used these values in the policy applies to the PPPoE tunnel.
Below is an example of the Splynx tariff plan with two additional fields and with the policy names specified:
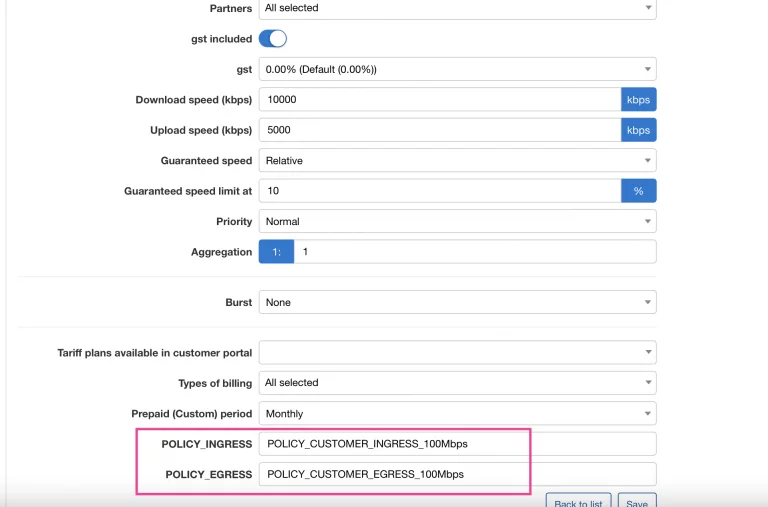
When a customer connects a PPPoE session, the value of the fields tariff_attributes.policy_egress and tariff_attributes.policy_ingress are taken and applied – in this case, POLICY_CUSTOMER_EGRESS_100Mbps and POLICY_CUSTOMER_INGRESS_100Mbps.
The policies should be defined inside IOS XR configuration this or similar way:
policy-map POLICY_CUSTOMER_EGRESS_100Mbps
class CUSTOMER_PREC_ALL
shape average 100000000 bps
queue-limit 1000000 bytes
!
class class-default
!
end-policy-map
!
policy-map POLICY_CUSTOMER_INGRESS_100Mbps
class class-default
police rate 100000000 bps
conform-action transmit
exceed-action drop
!
!
end-policy-map
!
Find out how Splynx helps ISPs grow
Learn more