



In the realm of network management, MikroTik is a popular choice for its robust features and cost-effectiveness. One of the critical tools in MikroTik’s arsenal is the NetFlow protocol, which enables detailed traffic analysis. With the introduction of RouterOS 7 and the end support of IP accounting, it’s important to revisit the relevance of NetFlow and how it can continue to play a pivotal role in network monitoring.
NetFlow is a network protocol developed by Cisco Systems, designed to collect and monitor network traffic. It provides a granular view of the traffic passing through a router or switch, offering insights into the source and destination of data, as well as the type of services being used. This information is invaluable for network administrators in troubleshooting, capacity planning, and security analysis.
MikroTik routers have the capability to export NetFlow data, which can be captured by various NetFlow collectors and analyzers. This allows administrators to gain a comprehensive understanding of how their network is being utilized.
Setting up NetFlow on a MikroTik router involves defining what traffic information should be exported and specifying the collector’s IP address. With this configuration, the router will periodically send NetFlow records to the specified collector.
With the release of RouterOS 7, MikroTik ends support IP accounting. This change brings forth a paradigm shift in how MikroTik routers handle accounting data, potentially affecting how NetFlow operates in conjunction with other monitoring tools. RouterOS uses the Netflow protocol and is called Traffic flow in Mikrotik devices.
The IP accounting, in previous versions, allowed external applications to retrieve real-time accounting data from the router. After the end of support of the IP accounting, MikroTik users now have more control over data privacy and security.
NetFlow’s ability to provide historical traffic data is invaluable for capacity planning. By analyzing trends and patterns, administrators can make informed decisions regarding bandwidth upgrades or optimizations.
NetFlow is an essential component of security analysis. It enables the identification of anomalies, such as unusually high traffic to a specific host or port, which could indicate a security breach.
When network issues arise, having access to historical traffic data can be immensely helpful in pinpointing the root cause. Administrators can trace through NetFlow records to identify when and where a problem occurred.
For organizations that need to adhere to regulatory compliance, NetFlow data can be crucial for generating reports and demonstrating compliance with data protection and security standards.
Splynx provides and supports setting up and using Netflow traffic accounting for Mikrotik routers and other network equipment manufacturers that do support Netflow protocol. Splynx is a collector and analyzer of NetFlow packets at the same time.
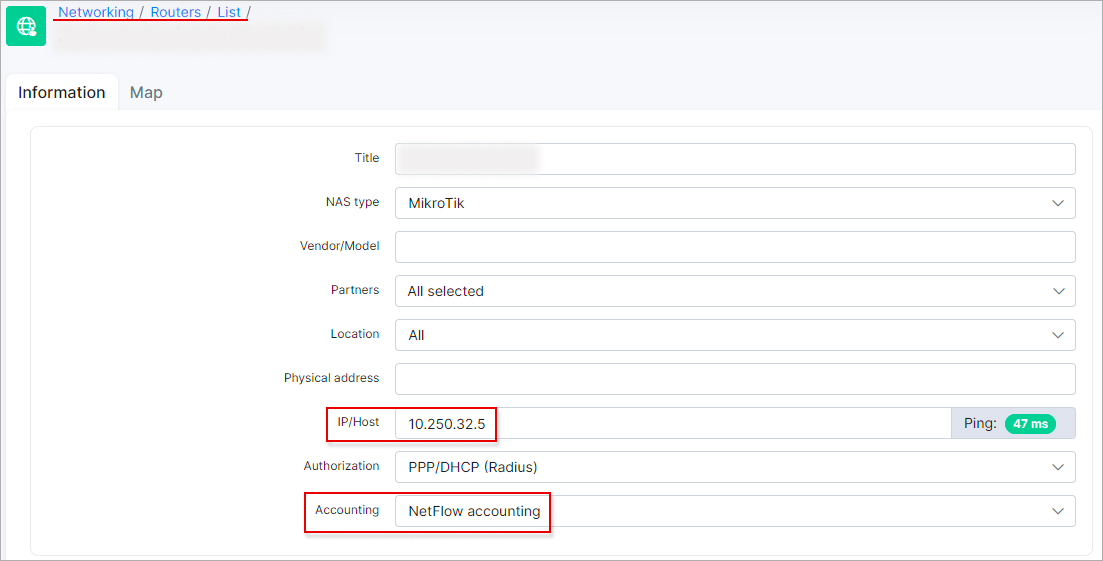
Step 1: Go to the Networking section, then click on Routers. Next, select the Add option, where you can input the router’s IP address and choose the desired Accounting type.
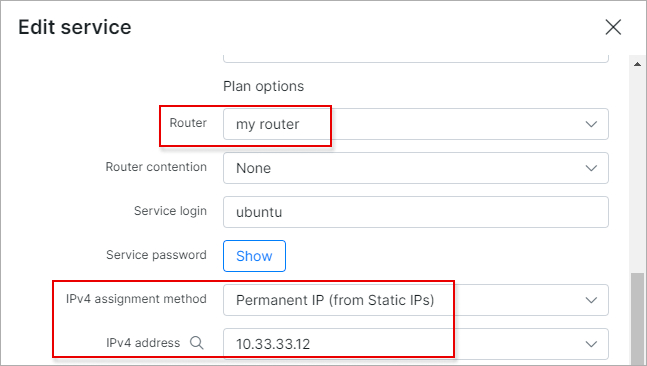
Step 2: Navigate to Customers → List, access the required customer’s profile, select the Services tab, and open the editing window for their Internet service. Input the router associated with this service, indicate the method of IP assignment (either from a pool or static), and provide the IP address details.
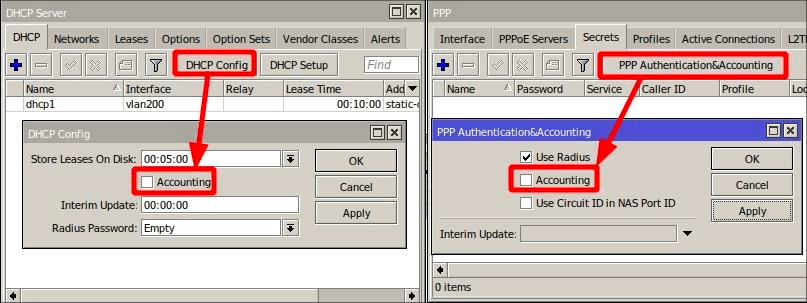
Step 3: If Radius authentication is employed on our router for customer authorization, we need to deactivate Radius accounting for services that should be tracked via NetFlow:
1. On the MikroTik device, go to IP → DHCP Server → DHCP (tab) → DHCP Config and turn off the Accounting feature.
2. In PPP → Secrets (tab) → PPP Authentication & Accounting, disable the Accounting option there as well.
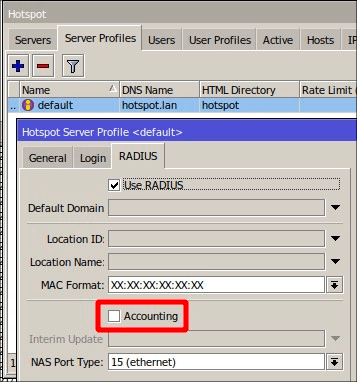
3. Go to IP → Hotspot, access the Server Profiles tab, select your profile, and turn off the Accounting feature.
Step 4: Access the MikroTik device and go to IP → Traffic Flow. Activate the option by ticking the checkbox and then specify a value in the Cache Entries field. Ensure that this value is a minimum of 128k, and you have the option to increase it if necessary, keeping in mind the router’s available built-in RAM.
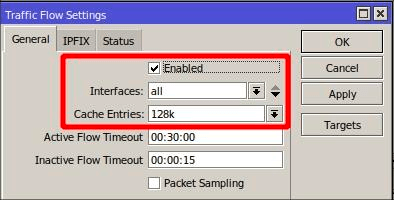
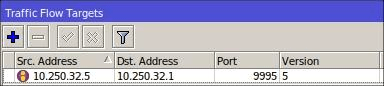
Step 5: On the MikroTik device, within the Traffic Flow Settings window, click the Targets button and include Splynx as the traffic flow destination:
Enter your Splynx IP address in the Dst. Address field, your router’s IP address in the Src. Address field, set the Port value to 9995, and choose Version 5 for the Version field.
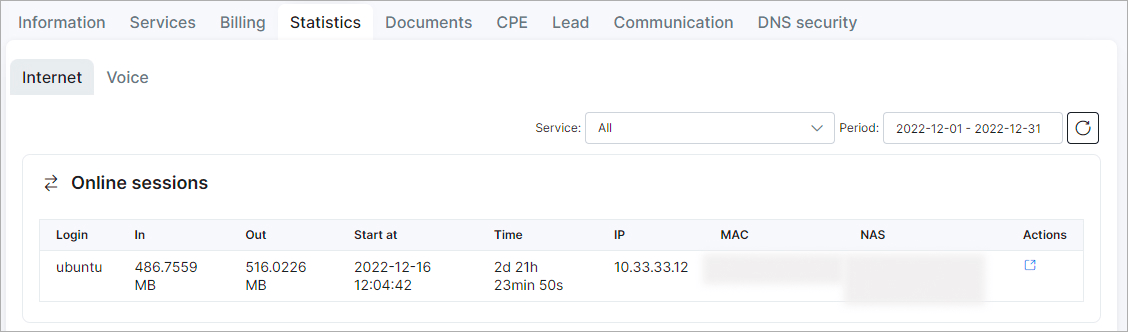
Step 6: After enabling Traffic Flow on the MikroTik router, allow a period of 5 to 10 minutes for the traffic data to become visible.
The traffic data will begin counting from the initially completed flow that MikroTik transmitted to the Splynx nfcapd collector.
You can also read an article about How to configure NetFlow accounting in Splynx on our website, as well as find more detailed information about the settings and the use of NetFlow accounting in our documentation.
Find out more about Traffic flow in Mikrotik devices here.
Despite the end of the support of IP accounting in RouterOS 7, the NetFlow protocol remains a powerful tool for network administrators using MikroTik routers. Its ability to provide detailed historical traffic data is indispensable for capacity planning, security analysis, troubleshooting, and compliance reporting. By leveraging NetFlow, administrators can continue to ensure the optimal performance and security of their networks in the ever-evolving landscape of network management.
Find out how Splynx helps ISPs grow
Learn more